Take Measures to Help Avoid a Ransomware Nightmare
Ransomware attacks — in which hackers break into private computer systems to encrypt and often steal files to hold for ransom — today are so prolific they’re considered a major national security issue. In 2020 alone, ransomware cost victims in the U.S. an estimated $1.4 billion.
Sadly, there is no shortage of instances, including attacks on Universal Health Services, which has more than 400 locations; The Colonial Pipeline, responsible for the country’s largest fuel pipeline; JBS, one of the world's largest meat processors; not to mention those on myriad schools, government agencies, corporations and small businesses. (Remember the hack of the software company Kaseya in July? It infected more than 1,500 organizations at once!)
With ransomware and other types of cyber attacks rising dramatically at a time when there is a worker shortage — meaning, not as many cybersecurity experts available to help victims get back online — is it paramount that you take steps to protect your medical, industrial and other embedded and connected devices.
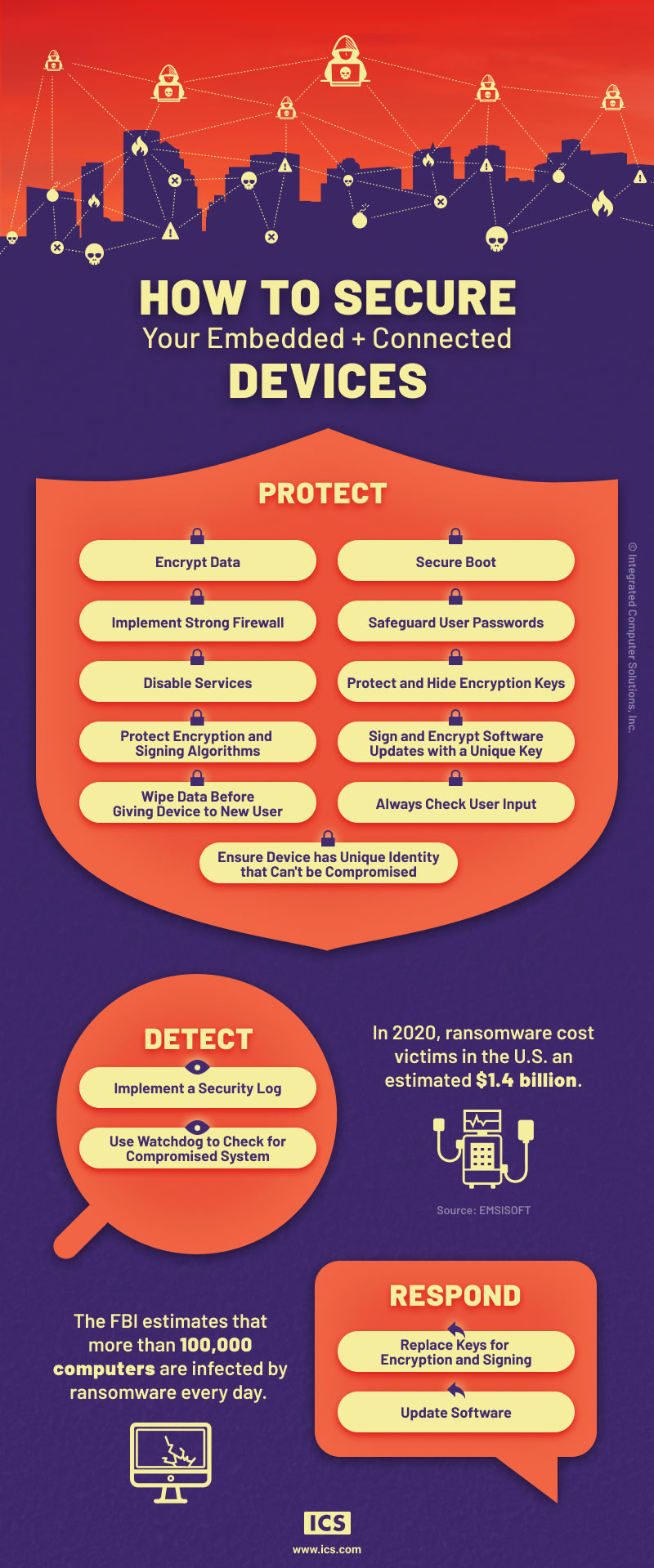
Ransomware can start with any security breach, including any weaknesses in your embedded and connected devices. To secure your devices, you need to take effective measures in three key categories: protect, detect and respond. Here’s a high-level look at some of the most essential.
1 PROTECT
Encrypt Data
Data must be encrypted both in transit and at rest, meaning all communications from/to your device must be encrypted so they can’t be snooped simply by monitoring network traffic. For data at rest, encrypt all protected health information (PHI) and personally identifiable information (PII) data when stored on the device, eIther through general storage encryption or database/file encryption.
Secure Boot
Ensure that only boot software/firmware signed by the manufacturer can boot the device. That means be sure to enable the secure boot functionality that comes with most modern platforms/microcontrollers.
Implement Strong Firewall
A firewall should be implemented and configured to only allow access to certain essential incoming ports.
Safeguard User Passwords
User passwords should expire after set time period, contain a minimum number of characters, and be required to contain special characters
Disable Services
All services associated with incoming IP traffic that could be used as an entry point should be turned off.
Protect and Hide Encryption Keys
Keys that are used in the encryption and signing of sensitive data should not be easily visible and should at minimum be stored encrypted. Consider using hardware root-of-trust where keys are never visible in memory.
Protect and Future-Proof Encryption and Signing Algorithms
The latest versions of known strong encryption algorithms should be used because they deliver higher levels of protection and will last longer against continuing advances in computing power.
Sign and Encrypt Software Updates with a Unique Key
All software updates should be signed to prove they are authentic and also encrypted to ensure against attacks that are possible through changing the contents of the software update. Only you should be able to provide a valid software update for the device.
Wipe All Data Before Giving Device to New User
Once someone has permanently finished using a device, it should be completely wiped of all PHI and PII hiding in all of the device’s data stores before being given to a different user since a new user can access all data on the device.
Always Check User Input
Whenever there is a text entry field, that text entry field should specifically guard against buffer overflows and/or SQL injection vulnerabilities.
Ensure Device Has a Unique Identity that Can’t be Compromised or Faked
A digitally signed identity can be used to ensure that the device is the only one with this identifier, which prevents anyone trying to represent a different device as being the one to upload data.
2 DETECT
Implement a Security Log
There must be a security log, which is continuously added to -- information on all events that might take on a security implication. Using a security log will allow you to periodically monitor the device to determine whether serious security events are occurring, and allow response. In other words, detect and respond.
Utilize a Watchdog to Check for Compromised System
A watchdog is another crucial component of your detect and respond system. If the device or network becomes unresponsive, the watchdog can kick in and alert a wider set of users, allowing for a robust response.
3 RESPOND
Replace Keys for Encryption and Signing
Ensure there is a mechanism to update keys stored on the device or to remove compromised keys, if necessary.
Update Software
New threats are emerging all the time. While it is impossible to guard against all future threats, the ability to react, by quickly updating software, will allow you to counter vulnerabilities yet to be discovered.
The Takeaway
Hackers are clever and highly motivated. The FBI estimates that more than 100,000 computers are infected by ransomware every day. Leave even the smallest opening, and cybercriminals can find a way into your system, take control, steal your data, even use one compromised device as a door into another. Even a fleet of others! Protect your network, data and reputation by carefully securing your embedded and connected devices. Read about device cybersecurity for the healthcare industry.